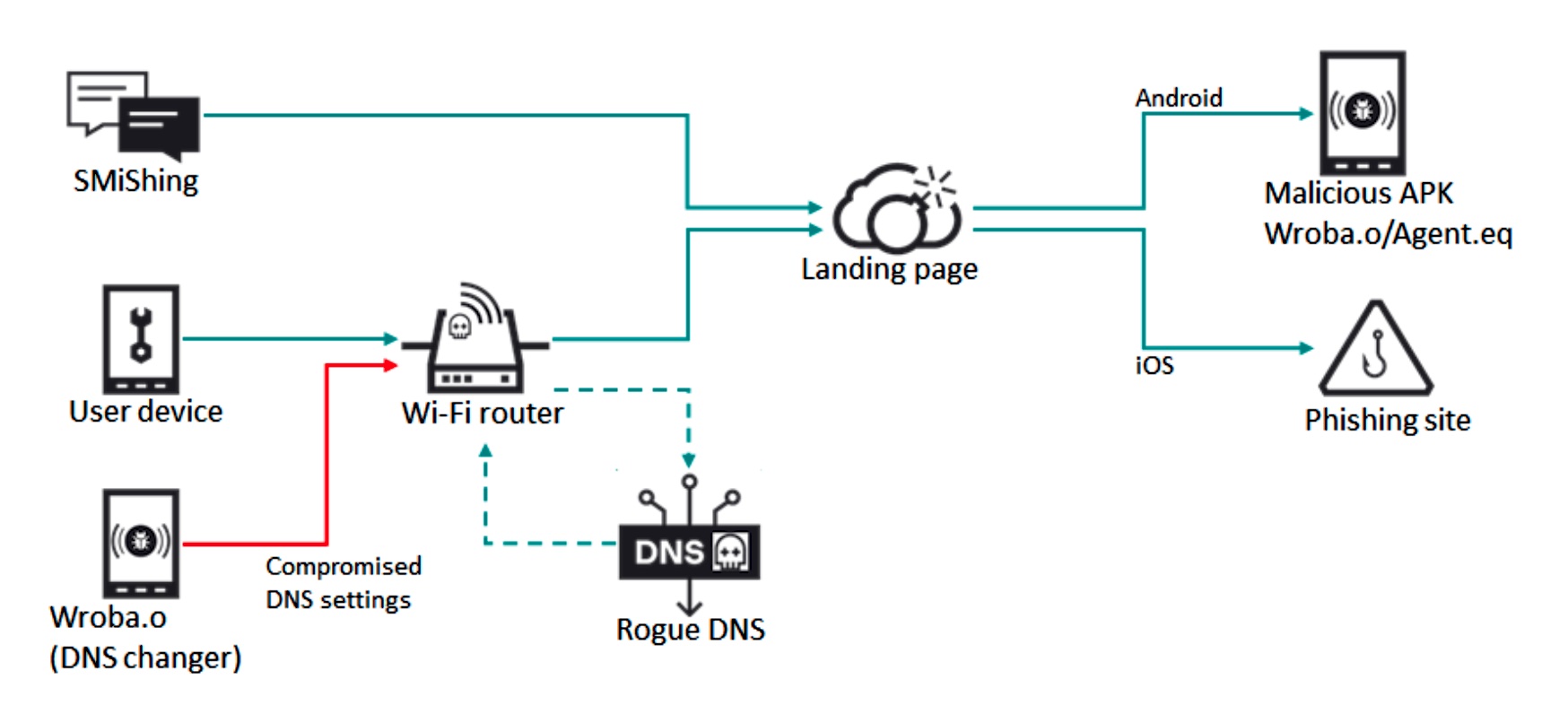
Researchers have uncovered a malicious Android app that can tamper with the wireless router the infected phone is connected to and force the router to send all network devices to malicious sites.
The malicious app, found by Kaspersky, uses a technique known as DNS (Domain Name System) hijacking. Once the app is installed, it connects to the router and attempts to log in to its administrative account by using default or commonly used credentials, such as admin:admin. When successful, the app then changes the DNS server to a malicious one controlled by the attackers. From then on, devices on the network can be directed to imposter sites that mimic legitimate ones but spread malware or log user credentials or other sensitive information.
Capable of spreading widely
“We believe that the discovery of this new DNS changer implementation is very important in terms of security,” Kaspersky researchers wrote. “The attacker can use it to manage all communications from devices using a compromised Wi-Fi router with the rogue DNS settings.”
The researchers continued: “Users connect infected Android devices to free/public Wi-Fi in such places as cafes, bars, libraries, hotels, shopping malls, and airports. When connected to a targeted Wi-Fi model with vulnerable settings, the Android malware will compromise the router and affect other devices as well. As a result, it is capable of spreading widely in the targeted regions.”
DNS is the mechanism that matches a domain name like ArsTechnica.com to 18.188.231.255, the numerical IP address where the site is hosted. DNS lookups are performed by servers operated by a user’s ISP or by services from companies such as Cloudflare or Google. By changing the DNS server address in a router’s administrative panel from a legitimate one to a malicious one, attackers can cause all devices connected to the router to receive malicious domain lookups that lead to lookalike sites used for cybercrime.


 Loading comments...
Loading comments...